flair Partners With Tugela People To Revolutionize HR Management
By joining forces, flair and Tugela People are providing a unified platform and support services to maximize the value of your HRIS investment.
- 11 Jul 2024
- Max 2 min read
The Number One HR Solution on Salesforce
The software as a service (SaaS) market is booming as it enables companies to access powerful solutions that help them operate more efficiently. However, when outsourcing business operations to third-party providers, security is always a crucial consideration. As SaaS vendors often process sensitive data, especially in the HR sector, it’s essential to verify that data is managed securely.
SOC 2 is one of the most prominent and trusted auditing procedures for service providers, establishing the level of trust required when choosing a SaaS provider. In this article, we will look at the specifics of SOC 2 compliance and why it is so important when it comes to cloud services.
SOC 2 is a compliance standard that service providers, particularly in the SaaS and cloud service market, can voluntarily undergo. It stands for System and Organization Controls but is sometimes referred to as service organization controls due to its relevance to service providers.
Developed by the American Institute of Certified Public Accountants (AICPA), SOC 2 provides a framework to ascertain that third-party service providers, including EOR service provider, have established reliable internal controls for managing sensitive information securely.
There are also other types of SOC reports, such as SOC 1 for financial controls. SOC 3 is similar to SOC 2, but designed for the general public. In contrast to other SOC reports, which are confidential, SOC 3 is less detailed and may be shared publicly to build trust with consumers. There are also specialized SOC reports for cybersecurity and supply chain.
As part of a SOC 2 report, external auditors verify whether a vendor complies with the five trust service principles defined by the AICPA. They will then issue the vendor an audit report. A successful audit (known as an unqualified opinion attestation) can help build trust among the vendor’s customers, business partners, and other stakeholders. A qualified opinion attestation, on the other hand, indicates that some areas may require attention.
In the US, SOC audits must be performed by an independent Certified Public Accountant (CPA) or an organization licensed by the AICPA and following its audit process guidelines. In the UK, members of the Institute of Chartered Accountants in England and Wales (ICAEW) are also permitted to carry out SOC audits.
Before undergoing a SOC 2 audit, businesses can take a readiness assessment. This is like a trial run, allowing organizations to identify any gaps in their security controls. In this way, they have time to remediate issues before the audit itself.
In creating SOC 2, the AICPA defined five Trust Services Criteria (TSCs). Service organizations undergoing a SOC 2 audit are assessed on their ability to meet the following criteria.
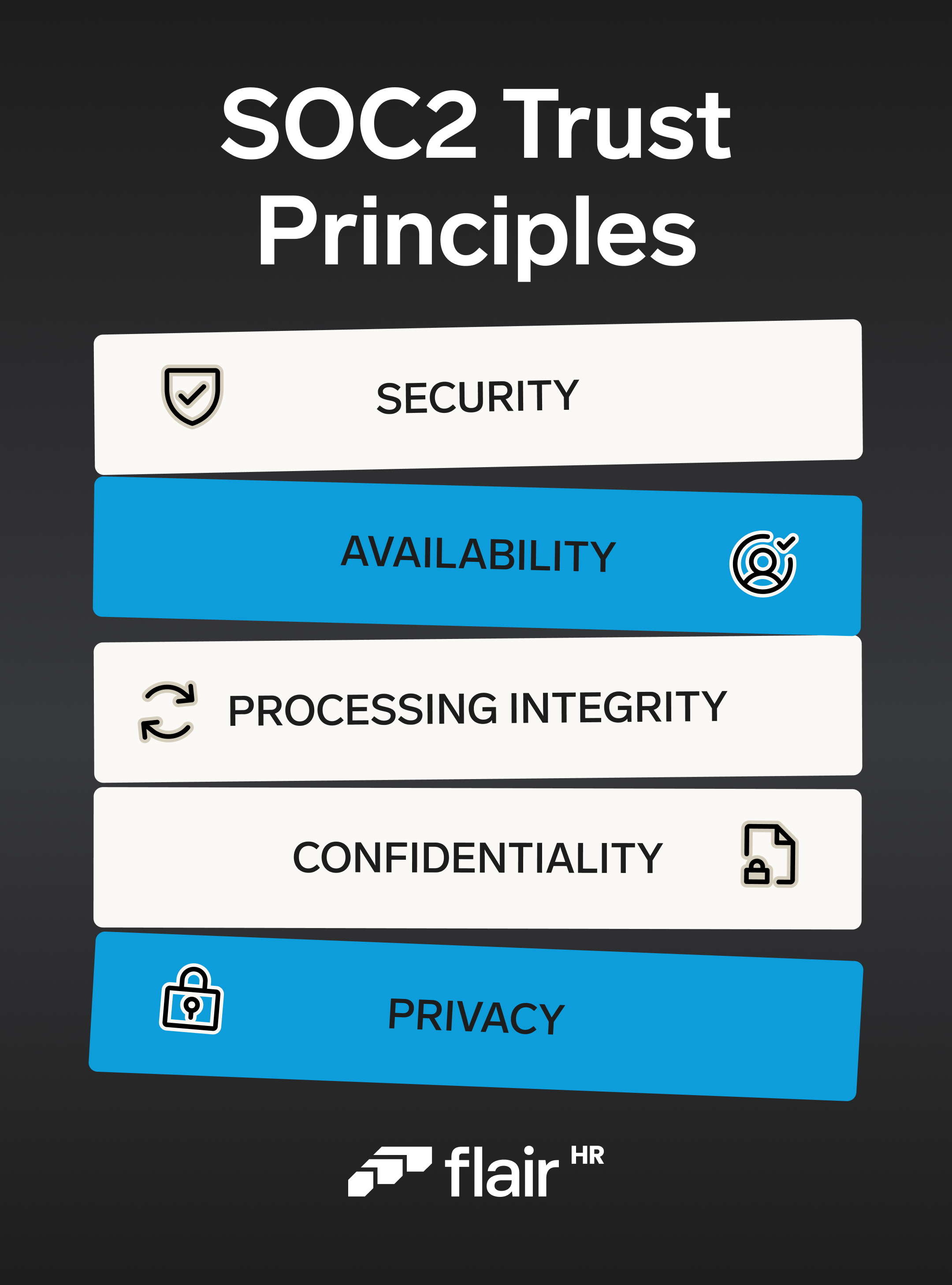
The Security principle is primarily about protecting data against unauthorized access and preventing data breaches. This can be achieved by implementing robust access controls, two-factor authentication (2FA), data encryption, and firewalls. Intrusion detection may also be used to identify security incidents and vulnerabilities in good time. Security compliance is the most important TSC and is mandatory for all SOC 2 audits.
Customers need to be able to rely on their service provider. Availability refers to the provider’s ability to keep its systems operational so that customer data is accessible when clients need it. The service provider and its customer may set up a service level agreement (SLA) to define the minimum guaranteed availability of systems. Performance monitoring is an important factor here, and IT disaster recovery procedures should be put in place to minimize downtime.
To meet this TSC, service providers must ensure that their systems process data accurately, reliably, and without delay. Process monitoring can be used to assure quality and comply with the Processing Integrity principle.
This principle is assessed on the ability of a service provider to protect information that is defined as confidential. For example, access controls and permissions can limit the number of people who are able to view sensitive information. Encryption at rest and in transit is another important information security measure to ensure confidentiality, and employees working for the service organization may need to sign non-disclosure agreements (NDAs).
Similar to the Security and Confidentiality TSCs, Privacy is about protecting information. However, the specific focus of this principle is the way that the service organization collects, uses, retains, discloses, and disposes of personal information. In particular, personally identifiable information (PII) is classed as sensitive data and must be protected accordingly.
After evaluating these criteria, the CPA will report their findings and their evaluation of the service provider’s security posture, privacy controls, and internal security controls. The attestation report includes an opinion letter with a summary of findings, a description of the organization’s systems and teams, and a description of how the auditor tested the organization’s internal controls.
There are two types of SOC 2 reports. A SOC 2 Type 1 report demonstrates compliance at a specific point in time, while a SOC 2 Type 2 evaluates security controls over a period of time between three months and a year.
Service providers often opt for a Type 1 report if they have recently made considerable changes to their data security processes. A Type 2 report covers the same areas that Type 1 does, but the audit is conducted over a longer period of time and details the operational effectiveness of security systems.

HR teams deal with large amounts of sensitive data. flair helps you protect this information with Salesforce-powered security automation and data privacy while improving the efficiency of your HR department and employees.
While SaaS solutions have a multitude of advantages for companies, you always want to make sure your data is in safe hands. Opting for a service provider that has undergone a SOC 2 audit means that the solution has been assessed by independent experts based on five Trust Services Criteria. The top benefits include:
As a SaaS HR solution provider, security and compliance are important values to us as flair. We hired Prescient Assurance, a licensed CPA firm, to audit our security practices, policies, procedures, and operations according to SOC 2 standards. Our SOC 2 audit report demonstrates that we manage data with the highest standard of security and compliance.
The auditor’s findings included:
All flair contractors and employees undergo background checks in accordance with local laws and industry best practices. They also sign non-disclosure agreements (NDAs) and take part in security training and testing. This ensures that a culture of security is embedded in flair.
All of our development projects follow secure development lifecycle principles. Any team members who are regularly involved in system development undergo annual secure development training, and our software development is conducted in line with OWASP's Top 10 recommendations for web application security. These recommendations are recognized by developers around the world as an important step towards more secure code.
We regularly deploy third-party penetration testing and vulnerability scanning on all production and internet-facing systems. As part of our software development process, we also perform static and dynamic application security testing on all code, including open-source libraries.
We protect customer data in line with SOC 2 standards of encryption in transit and at rest. Role-based access controls and least-privileged access principles keep data secure. All customer cloud environments and data are isolated, and each customer environment is stored within a dedicated trust zone to prevent any accidental or malicious co-mingling.
When dealing with HR and recruiting data, it’s vital to ensure that it is secure. That’s one of the reasons why flair is built natively on Salesforce, the world’s leading CRM platform. Salesforce is not only powerful, highly scalable, and customizable, but it is also protected by advanced security technology.
Salesforce’s role-based access controls and permissions are ideal for HR teams, as they can be configured to ensure that users only see the data they need to do their jobs and they protect against unauthorized access. This is particularly helpful for organizations operating in multiple countries or with multiple entities and subsidiaries.
The Salesforce platform also encrypts data in transit and at rest. Security automation technology and threat detection provide an additional layer of protection. What’s more, Salesforce Backup prevents data loss in the event of accidental deletion or cyberattacks.
As a certified Salesforce partner, we provide a highly secure HR solution that can help you comply with regulations such as GDPR and HIPAA. Our successful SOC 2 audit is proof of our commitment to keeping our customers’ data safe and ensuring responsible security practices in development, testing, and delivering our solution.
Working with clients in a wide range of countries, we are well-versed in the specific security and compliance standards around the globe and in different industries. Talk to one of our product specialists to learn how flair can help you achieve your HR compliance objectives.
Join flair’s newsletter to receive the latest tips & trends in the HR world.

